Introducing the New Risk Monitor for Security and Compliance

“You can’t protect what you don’t see,” as the old security adage goes. This is why IT asset management (ITAM) is – and has been – a crucial first step in managing an organization’s cybersecurity posture. Without a complete inventory of the IT environment, it’s impossible to see where the potential vulnerabilities and risks reside.
The role of asset management has gained visibility as mega-breaches impacting the likes of Equifax dominate the news cycle. And increasingly, cybersecurity frameworks like those offered by the National Institute of Standards and Technology (NIST) and the Center for Internet Security (CIS) mandate that asset management plays a role in upstream best practices for security programs.
As IT estates proliferate, the impact of a comprehensive inventory will only increase – in volume, in complexity, and in the types of data it must touch. Technology intelligence is at the heart of Snow’s mission, and our Risk Monitor product leverages the rich data and insights compiled by asset management to combat cybersecurity and data privacy risk.
The Evolution of Asset Management & Cybersecurity
Traditionally, the role of IT and software asset management practitioners has revolved around tool audits and cost controls. But as cybersecurity practices have evolved, inventory and normalization have become a crucial first step in managing risk. We’re entering an age where IT teams are transitioning from the “software police” to “enterprise architects,” with the opportunity to deliver business impact beyond the realm of simply assets.
To do this, IT and asset management professionals must work hand in hand with security teams – sharing insights about the IT environment along with the right context to make decisions about how to prioritize and remediate risks. The risk landscape can be endless (and cyberattacks are a matter of “when,” not “if”), and in order to protect themselves, organizations must build their cybersecurity programs on a foundation of robust, normalized, contextual data.
Practically speaking, businesses will want to embed positive practices from asset management into their cybersecurity processes. In fact, Snow has facilitated this for a long time by providing complete visibility and manageability over an organization’s IT ecosystem, because of the fact that basics of asset management are key to a successful cybersecurity program.
From Visibility to Action
We are taking this critical collaboration between ITAM and security to the next level with Risk Monitor, the only solution that uses the same discovery agent for both asset management and vulnerability identification. This approach provides organizations with a single source of truth that is augmented with trusted third-party as well as proprietary first-party data.
- The full IT landscape in context. By capturing the extent of what assets, software, applications and cloud instances are in the IT environment, businesses can close the gaps on risk – and prevent entry by motivated hackers. Building upon Snow’s industry-leading inventory and normalization technologies, Risk Monitor helps you manage risk by automatically providing a comprehensive and contextual view of where high-stakes vulnerabilities and personally identifiable information (PII) liabilities reside.
- Proactive management of EOL applications. At any given time, an organization might have thousands of vulnerabilities. It’s nearly impossible to address them all, which is why businesses must prioritize remediation. End-of-life (EOL) applications, however, are especially critical as they can create significant exposure. Risk Monitor showcases both risk ratings and EOL information in one place, which speeds up time to remediation and informs decision-making in an actionable way.
- Visibility of open source applications. Because open source code doesn’t require licenses, it’s an element of the IT estate that traditional SAM functions often don’t review. But open source can supply some of the greatest vulnerability risks since there’s no proactive notification of vulnerabilities and patching. As such, an effective SAM practice will help identify open-source risks upstream, so they don’t cause problems down the road.
The ability to get an integrated view of technology intelligence across software, hardware, SaaS and IaaS makes the Snow platform valuable for more than just spend optimization.
With Risk Monitor, businesses can view technology intelligence through the lens of security, and use that visibility to inform their security programs.
Risk Monitor Features
Interactive Dashboard Provides Actionable Insights
Managing the IT environment is increasingly complex – as employees focused on productivity access SaaS-based tools in a distributed procurement model for software.
With Snow’s agent-based approach, IT teams can feel confident they have an accurate picture of what’s actually happening in the estate. We also bring in vulnerability data from the NIST’s National Vulnerability Database and augment this with a proprietary database of software and applications that may process personal data, to give organizations the most informed intelligence to prioritize their next steps.
A central dashboard helps you prioritize remediation with a variety of contextual, actionable insights such as:
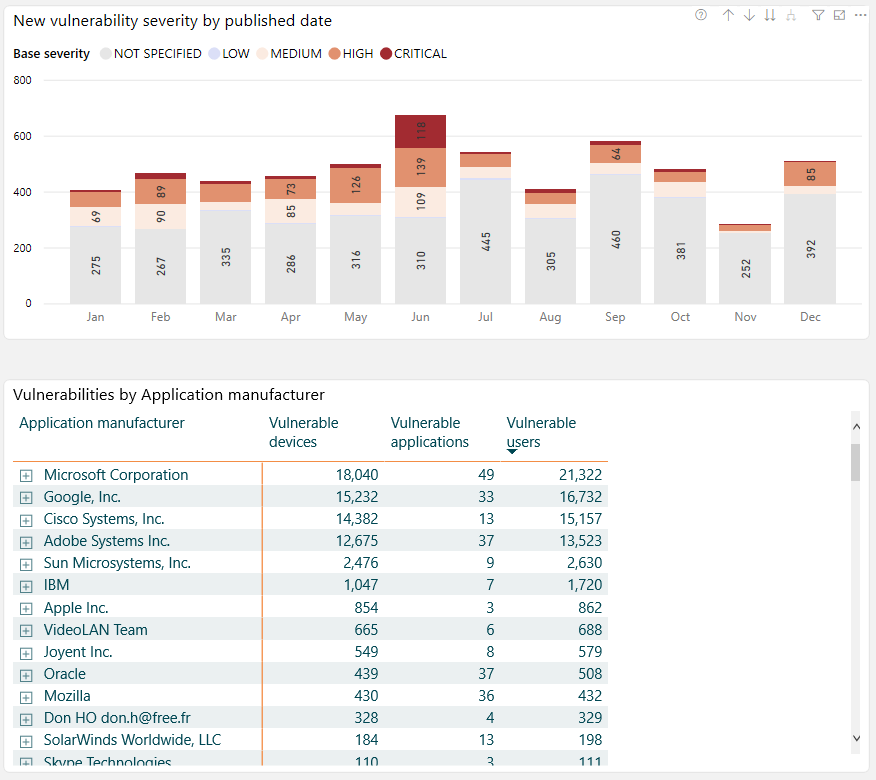
- Where software vulnerabilities are located in your IT environment
- The severity level of software vulnerabilities identified per the United States’ NIST National Vulnerability Database
- How vulnerable apps are being used
- Contextual information to help you prioritize which vulnerabilities to address first, and go straight to the problem (e.g. device, department, user, and more)
And interactive capabilities let you explore and discover what lies in the estate – and what attack vectors might be exploited.
Near-Time Data Helps You Respond Quickly
Risk Monitor leverages the recognition of over 600,000 software applications, updated daily, for near-time insights into your risk landscape. Many vulnerability assessment tools rely on a monthly scan – which can be insufficient when you need to respond quickly to new threats and changes in your IT environment.
Map of Apps Containing PII Facilitates Regulatory Compliance
Risk Monitor identifies what software apps are designed to do – and if that potentially includes housing or processing PII that is subject to regulatory compliance and reporting.
Often, organizations lack the resources to effectively gather information about where personal data is stored. But with Risk Monitor, you can quickly pinpoint which applications may require attention for both remediation and reporting. The ability to gather this information also facilitates the Record of Processing Activity (ROPA) for GDPR.
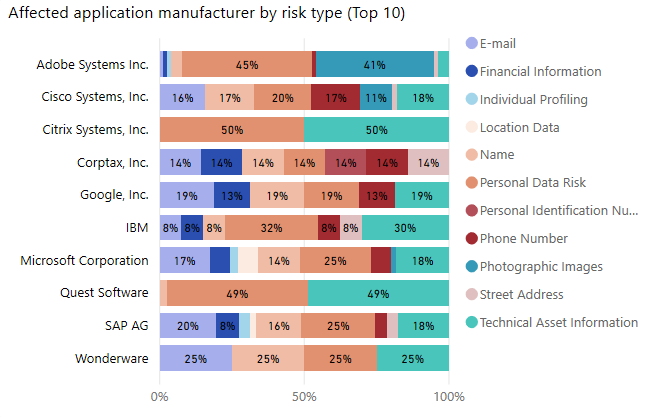
By providing a holistic view of the IT environment, Risk Monitor will help IT teams and security professionals see where risks are present, so they can protect their organizations with the right tools, remediation and processes.
Click here to learn how to strengthen your security programs with Snow’s Risk Monitor, providing comprehensive visibility into your risk landscape.