Addressing Vulnerability False Positives with Risk Monitor 2.4

The past year has proven to be a real challenge for vulnerability risk management. The rise of easily downloadable cloud technologies, increased business-led IT purchasing and the move to remote work environments introduced unprecedented levels of risk for IT teams. Many organizations opened the floodgates to new technologies to maintain business continuity during the pandemic and keep remote teams productive.
As a result, IT teams are left to defend against a growing number of high-priority security threats from newly deployed software and shadow IT. We’re excited to share that our most recent Risk Monitor release, Risk Monitor 2.4, offers expanded capabilities for identifying and separating false positives from real vulnerabilities – making it easier for IT teams to manage risk and save time. From Snow’s reporting alone, Risk Monitor has been able to remove over 274 million false positives.
Security is a top priority
In Snow’s 2021 Priorities Report, 38% of IT leaders surveyed identified one of their top three top priorities as reducing security risks. And, over the past 12 months, 43% said that cybersecurity threats were one of IT’s biggest challenges.
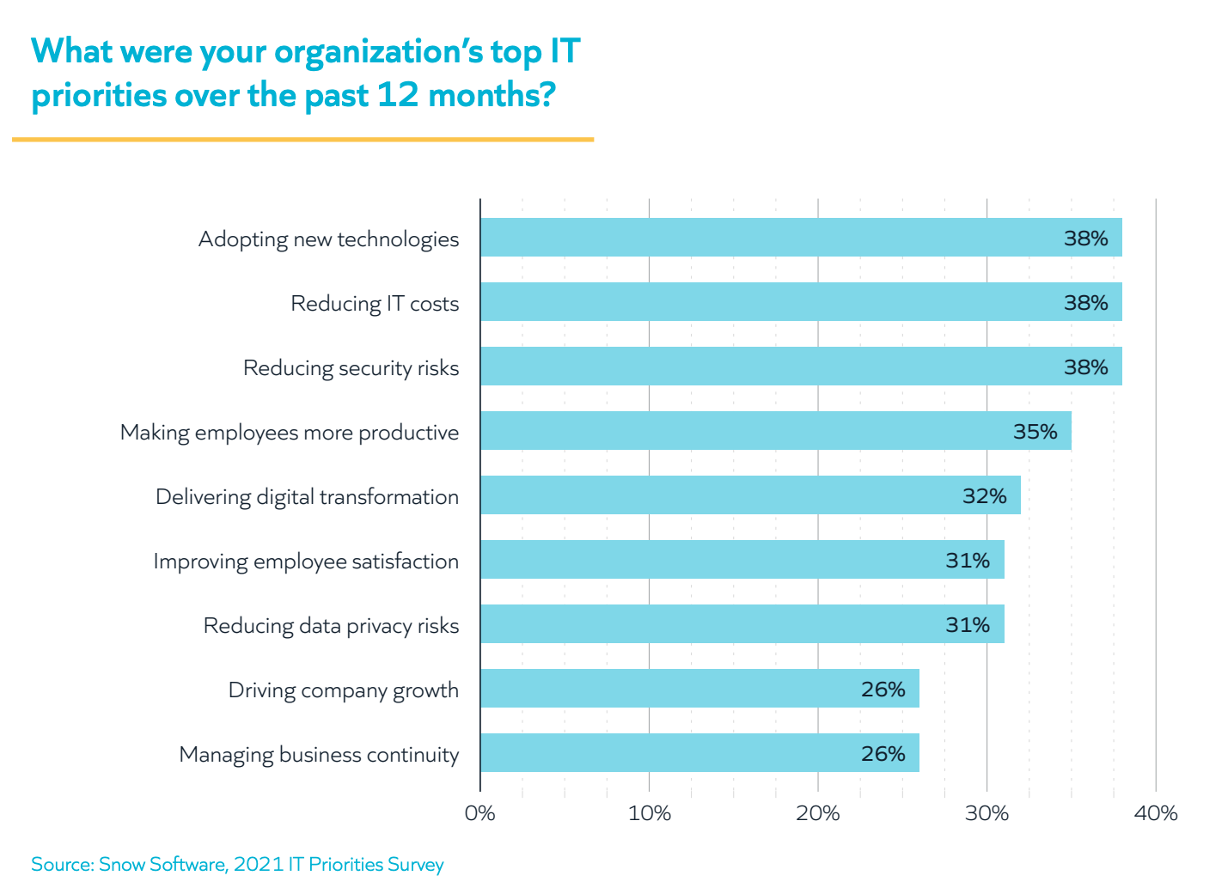
To address these security concerns, we explored how security teams are currently keeping up with risk.
Security teams use cybersecurity tools to assess where their risk is. But when it comes to vulnerabilities, most of their time is spent addressing actual risk to operations (true positives) and combing through false negatives, which are the ones that sneak by as not posing risk, when in fact, they do.
Managing false positives
Another chunk of vulnerabilities appears in the form of false positives; a false positive is like when your Nest or Alexa alert you there is motion in the room, but the room is empty. Reviewing false positives requires inspecting each alert and signing off. A lot of time is spent going down the list, analyzing it one by one.
Risk Monitor provides complete visibility across the enterprise, making it easy to see how many devices are in use; where they are; which applications are installed and who has access to them across on-premises, cloud and mobile devices.
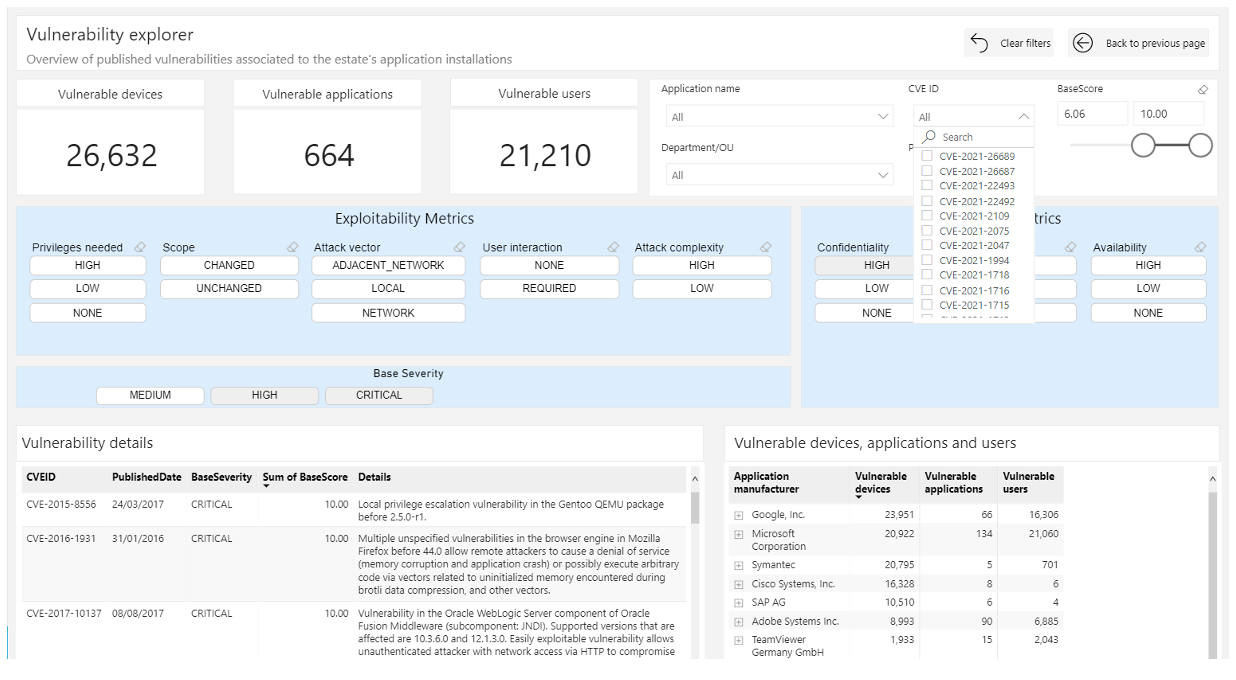
This powerful inventory data is augmented with data from the National Vulnerability Database and displayed on an intuitive dashboard to pinpoint where critical vulnerabilities reside in your environment.
Vulnerability management that goes above and beyond
In addressing common headaches that stem from Windows 10 vulnerabilities, Windows 10 versions are now recognized as patching previous vulnerabilities. With the deployment of the Windows Update agent script, reports now accurately reflect any applied patches. In a sample of one Windows 10 machine, Risk Monitor consolidated the list of vulnerabilities from 1600 to 12 by reducing the number of false positives identified. This saves time and energy and ensures that IT is only paying attention to the actual risks in the environment.
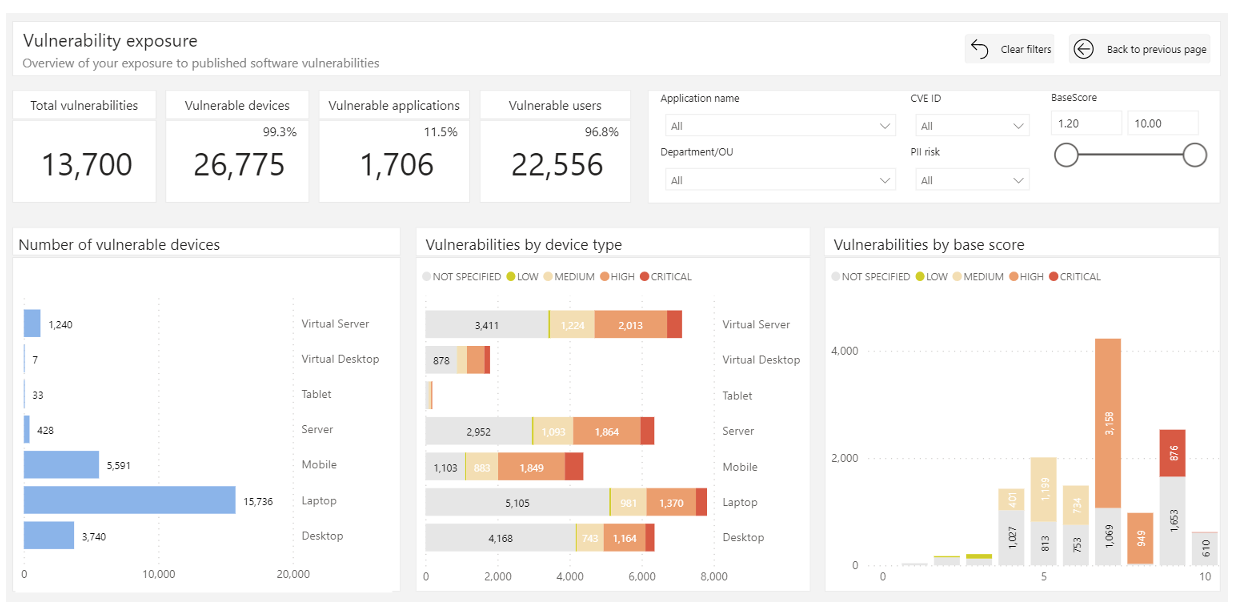
Additionally, Risk Monitor 2.4 has significantly improved the speed and performance of viewing and filtering the reports. There is also enhanced recognition of software versions in all applications, further reducing the number of false positives reported.
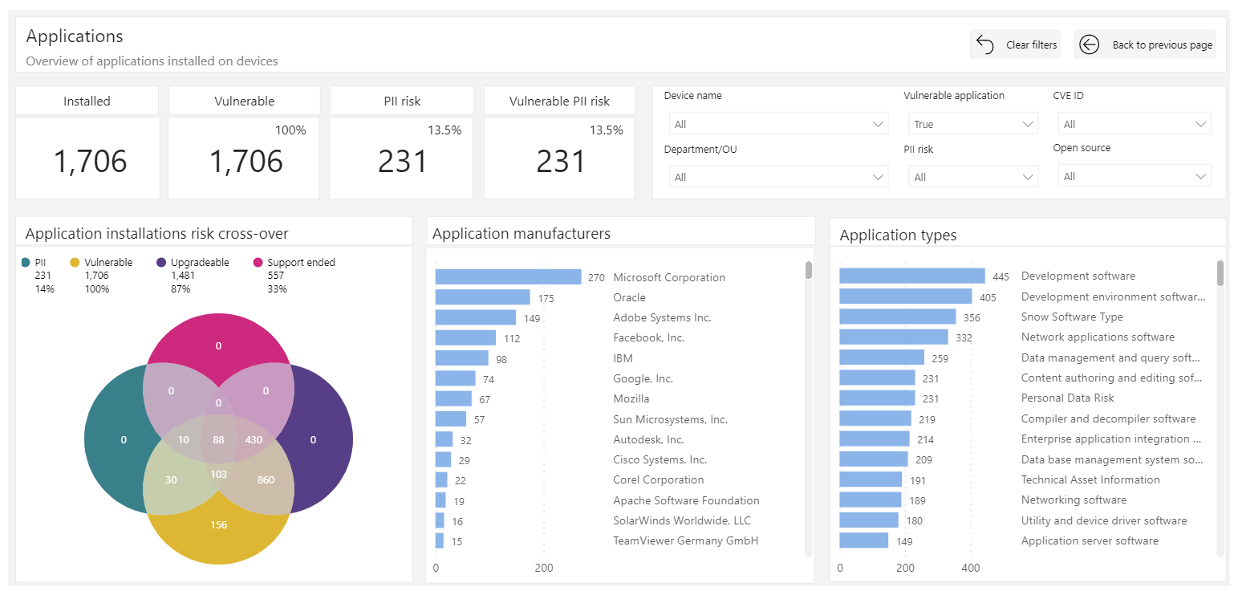
Learn more about how Snow Risk Monitor can help you simplify handling false positives and strengthen your company’s risk management strategy.