Patching the Meltdown/Spectre data leak

The IT world of 2018 woke up to an unwelcome bang in the form of Meltdown and Spectre – two widespread hardware vulnerabilities. To encapsulate the problem, which security experts have classified as catastrophic, billions of computers and devices are at risk as the vulnerability exposes the data stored in the most protected part of a device’s hardware; the place where passwords, encryption keys, and other credentials are stored.
The ensuing headache for IT managers and security personnel has not been to figure out if the systems they are responsible for are vulnerable – because they are. But to figure out the extent to which the many patches needed to dampen the threat posed by Meltdown and Spectre have been installed.
The backdoor that Meltdown/Spectre opens to would-be attackers is unlike anything the IT security world has previously witnessed. The wannacry ransomware worm, for example, which caused millions of dollars’ worth of downtime in major systems in May 2017, exploited a flaw in an out-of-date version of the Windows operating system – for which Snow released a script to gain insight into the reach of the worm.
By stark contrast, the Meltdown/Spectre vulnerabilities exploit a performance feature purposely built into hardware design – significantly in Intel processors as well as AMD, ARM, and Apple. With a far greater attack surface than the wannacry worm, Meltdown/Spectre has had vendors scrambling to release patches.
What we don’t know at this time is:
- If an attack has been carried out that exploits the Meltdown/Spectre vulnerabilities
- How to detect an attack – the vulnerability can be exploited without leaving a trace
What we do know:
- Vendors are continuing to release software patches to protect against the Meltdown/Spectre threat.
- Figuring out to what extent your organization has been patched is a complicated time-consuming process.
Rumors abound that the software patches degrade system performance by up to 30%. But I would say, that that’s something organizations need to be prepared to manage, while chip manufacturers return to the design table to address the vulnerability. But it’s going to be many years before all the chips used in the billions of devices across the world have been replaced, if that is even feasible. So, the best solution is to manage the threat.
And that’s where Snow comes in. Just as our software helps to protect your organization from risk in the form of unpaid license fees, shelfware, audit fines, and inaccurate software budgeting, the data provided by our agents will ease management of the risk posed by Meltdown/Spectre.
Assessing the level of risk posed by Meltdown/Spectre to your organization, needs to be addressed on different levels: the hardware, the operating system, and applications. You need to be able to determine what endpoints in your estate are affected based on the processor type they are running, the operating system version, and the level of patching implemented on applications that are affected, like web browsers such as Google Chrome, Microsoft Edge, and Mozilla’s Firefox.
The good news is that Snow agents already extract the hardware, operating system, and browser version information needed to determine the extent of your risk – all packaged in a customized Snow License Manager report called RISK Meltdown/Spectre (as shown in Figure 2). For customers running Windows, we have made an additional script that can be used by our agent, enabling it to automatically detect the patch status of the Windows operating system by running the official script provided by Microsoft, and capture the result as part of the inventory scan. This agent script add-on and the customized Snow License Manager report is available on-demand to our customers using Snow Inventory (3.x and 5.x), Software Recognition Service, and Snow License Manager (8.x). As our products communicate with all inventoried machines over the internet, our solution overcomes the issue of detecting the status of remote machines.
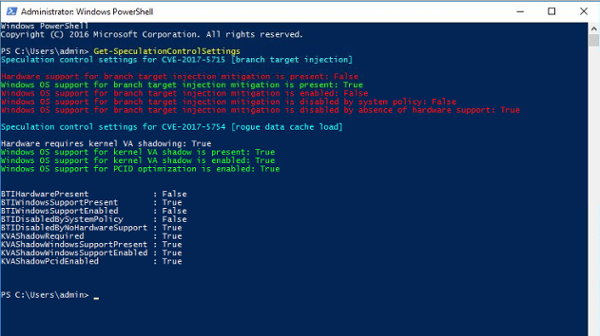
Figure 1: Official assessment script provided by Microsoft:https://gallery.technet.microsoft.com/scriptcenter/Speculation-Control-e36f0050
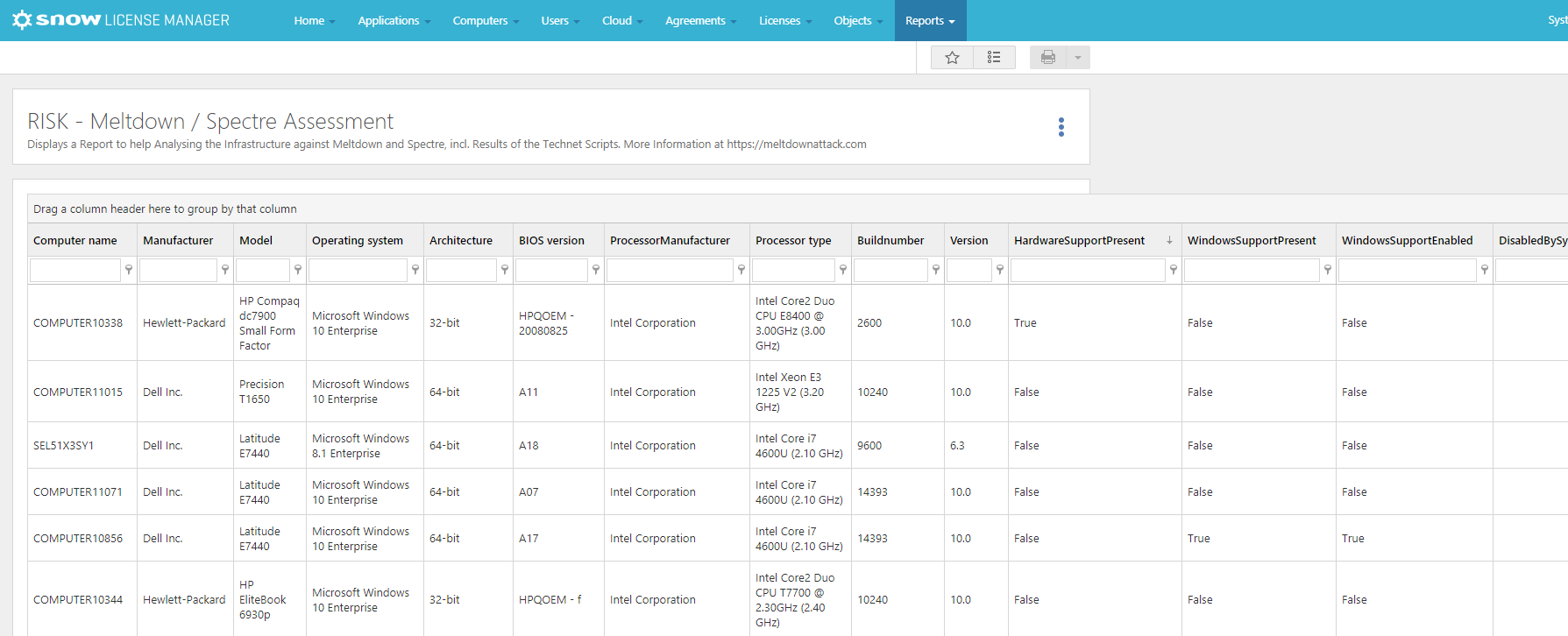
Figure 2: Customized Meltdown/Spectre Report in Snow License Manager
FOR MORE HELP
All Snow customers affected by this attack and any others interested in how Snow helps customers maintain and optimize their IT estate are encouraged to reach out to us for additional information.